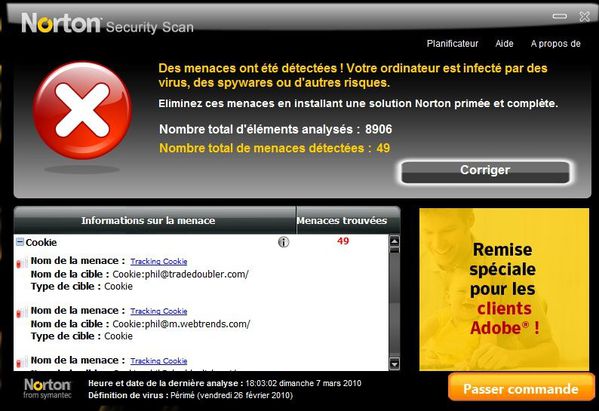
I'm not gonna deal here with the real McAfee DAT 5958 issue by itself. What I find interesting is what's coming around this incident.
Some other AV vendors warned that users attempts t download the DAT that fixes the 5958 failure may be used to infect their computers.
I was honestly thinking about fake DAT packages: malware linked to a real exefile DAT from McAfee, or even just malwares called 'SDAT5959'...
But what I discovered is actually worse, to me.
Consider the following Google request: download mcafee DAT 5959. Quite natural and obvious, isn't it?
Here is the URL of the 5th page:
http://www.google.fr/search?hl=fr&safe=off&q=download+mcafee+DAT+5959&start=40&sa=N
But this is where the danger shows up. Let's have a look at the first link of the Google's page of results:

The website domain name is: tolstiy.co.cc.
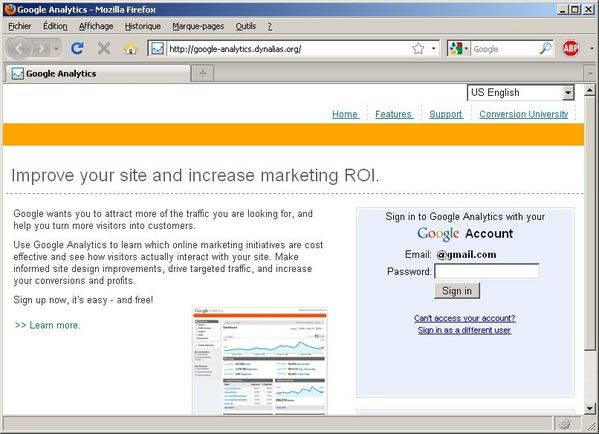
The Google preview of its content even includes the Google logo.. This should not be dangerous, right?
You may notice all the relevant keywords the website may need to be well indexed and appear at a good place in Google's results: 'sdat 5959 free download license mcafee superdat failure SDAT5959 EM. exe mcafee8.5i, McAfee®: 5960 Update '
This could help SEO hijacking (or poisonning) for sure!
Nonetheless the point is that the user will immediately be redirected to another website: endroiturlredirect.com

Then the malicious part shows up. This pages hosts an exploit!
Avira prompted then a warning:
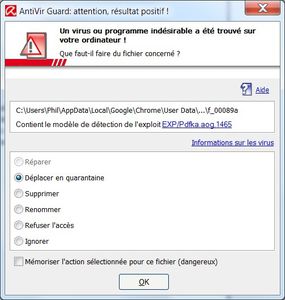
A PDF exploit for a DAT update rescue... that's probably funny (or weird).
Therefore I strongly recommend to any users and admins to really pay attention to where they download updates (including antivirus ones), at any time, especially in case of emergencies.
More about the website: http://tolstiy.co.cc/
You have to pay attention to notice something quite strange.
I said that the thumbnail of it seems to include a Google's logo... yes but guess what, the Google logo, buttons and request bar are all a simple picture in fact!
And here is the URL of it: http://www.webopedia.com/quick_ref/img/google_screen001.jpg
And what about the WhoIs of it? http://www.domaincrawler.com/domains/view/tolstiy.co.cc
Hey, more interesting: the IP address seems to be a Brazilian one, and the rest of the WhoIS info appears to be protected by an anonymization system. Quite obscure, but a kindda habit in VX methods.
But what if I use Internet Explorer 8?
Surprinsingly (or not?) the page redirected me to: malware-checker-free.com. And I.E. 8 screamed about a phishing risk while accessing this website.
Here is a screenshot of what I saw:
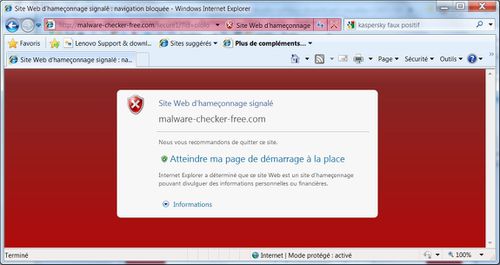
And what about other browsers? (PoC: Win 7, 64 bits, full patched).
- Safari (last version) did not alert me in anayway
- Firefox 32 & 64 bits (last versions): no alert
- Opera 10 (last version): no alert.
- Chrome (last version) : no alert.
So here is what an user could see if he does not use I.E.:
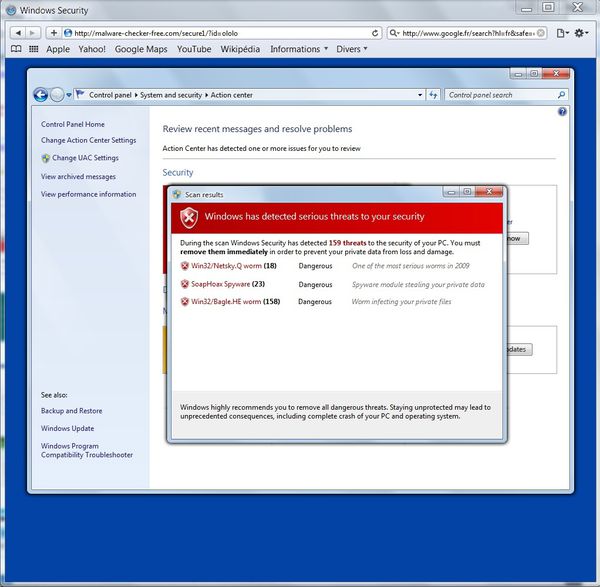
And the (funny but) annoying part of it is an endless loop behind this popup:

Whatever an user will do ('cancel', or 'OK'), the popup will come back, and furthermore will try to download an exefile on the computer.
This file is called: 'win_protection_update.exe'
Here is the VT results for it (let me remind that VT is a list of command line AV scanners, not the realtime protection they could offer in a regular installation):
http://www.virustotal.com/fr/analisis/415af935f5ce82f68f15ad133af4542813e34c40a7c5825fed9cdf0d2a46d304-1272584528
Ok so that's 20 out of 41 engines, not bad.
About the malicious URL by itself: http://malware -checker -free.com/secure1/?id=ololo
If you try to access it with only the FQDN, let's say malware-checker -free.com you may be redirected to... Google. A bit funny.
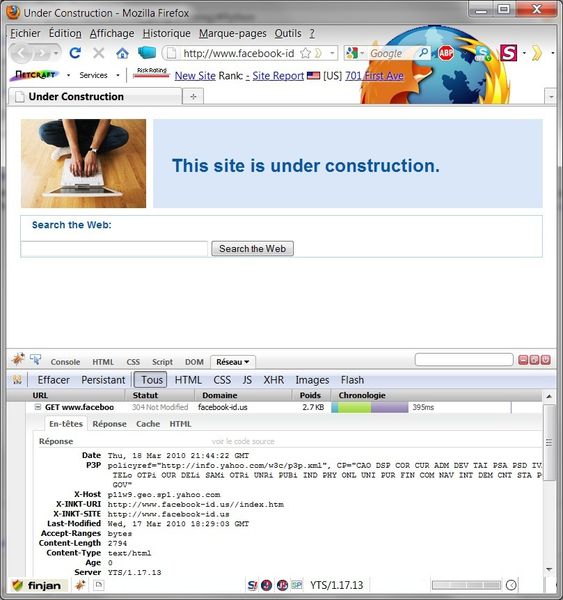
But if you try to change subdolder and/or page, such like: http://malware -checker-free.com/test here is what shows up:
Apache/2.2.3 (CentOS) Server at malware-checker-free.com Port 80
Either the bad guys forgot to update (and secure) their web server, or they hacked a third party one to host their malicious page and files...
Last, if you look at the source code of the webpage http://malware -checker-free.com/secure1/?id=ololo (thanks to Opera!), you may have an idea about how the bad guys tried to obfuscate their source code:
<!--
Page protected by ionCube - HTML/JavaScript Encoder
Copyright (c) 2003 RWJD.Com and ionCube Ltd. All Rights Reserved.
Any analysis of this source code, embedded data or file by any means and by any entity whether human or otherwise to including but without limitation to discover details of internal operation, to reverse engineer, to de-compile object code, or to modify for the purposes of modifying behavior or scope of their usage is forbidden.
-->
To finish with, a Google request will suggest that ionCube is a proprietary solution to "protect and license" the PHP pages... well, I'm not sure the bad guys did pay for the ionCube license (just guessing).