To those who still believe that downloading a file from "common downloadZ websites", here is (another?) kindda sample of how dangerous it can be for your computer...
First, the video file displays the following message in the Windows Media Player (or in VLC, if it's your default mediaplayer):
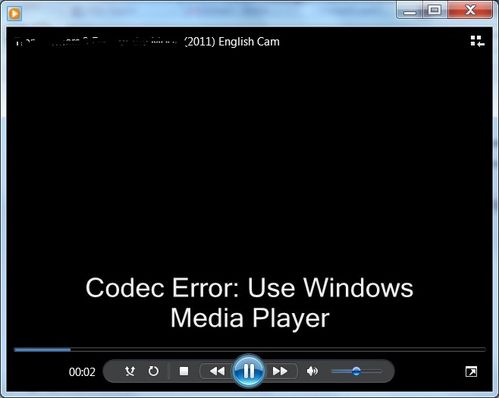
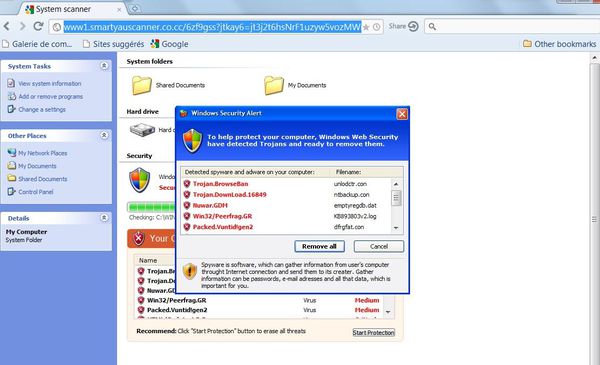
But at the same time, it will launch your default web browser:
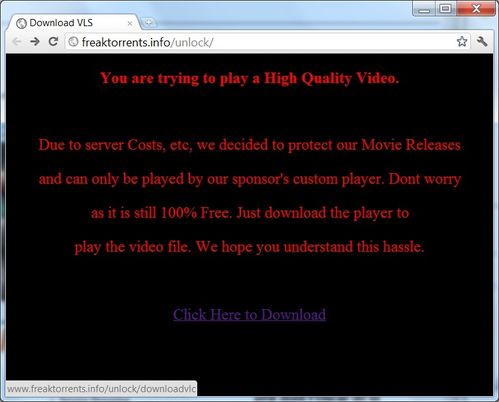
The text "you are going to play a High Quality Video" seems only to be there to tempt the user...
As you can see, the link at the bottom of the page points to: freaktorrents .info/unlock/downloadvlc.
In fact, it will drive the user to:
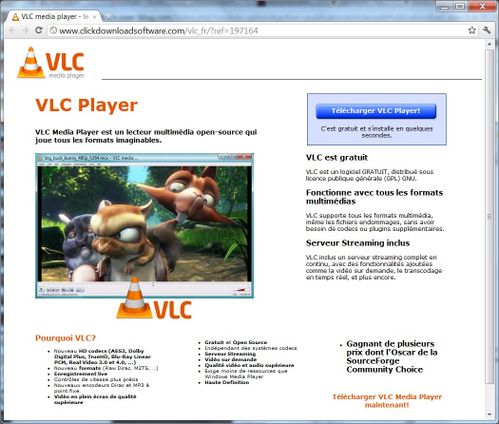
Please note that the website will automatically translate to your language (the one of your browser).
What about the VLC they offer in "free download"?
Not only it is an obsolete version according to the filename:
http://preview.licenseacquisition.org/48/1056428137.51143/vlc-1.0.1-win32.exe
In fact, once the download has started, the last version of VLC arrives on the computer.
But there is another file behind the "download" blue button:
http://origin-ics. clickpotato.tv/IC/GPLCPLite47/16866/0/3a9517da-aa34-46a5-ba0b-72db30c78707/VLCSetup.exe
it is not the real VLC, it is most likely a downloader, which is pretty well detected by VirusTotal! 26 engines out of 42... But surprisingly, neither Panda Cloud nor Immunet Cloud did detect the sample!
http://www.virustotal.com/file-scan/report.html?id=0c8a5c2a1d472d2b5f7ed0a8f8c63f38acc051416967dc48e43917d88ec96717-1304978623
I find it interesting that this URL seems to appear only once... Probably they record the IP address of the visitor. Typically a VX trick.
So, please keep in mind not to download media files from untrusted websites!
Let's talk a bit more about the vlcsetup.exe:
The funny point I think is that the file is digitally signed! (Pinball Corp, what a name...)
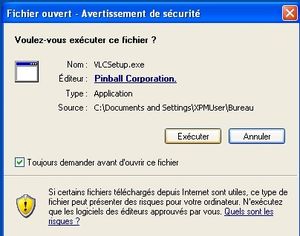
Even legitimate software are often not digitally signed... anyway, the dark side also uses tools to drive user confidence.
Once the file is being run, here is the network traffic it creates:

One request is somewhat interesting:
POST /generate/software/?SAIRND=233525&icbrandid=10&os=5.1&browser=IE.6.0&hdid=00-03-FF-4B-E1-AF&cc=FR&chid=197164&cid=1315344&con=n&ix=gplcplite&v.installername=VLCSetup.exe&v.method=software&v.s=65536&v.rascsi=n&realplayer.code=0&rpwcdesktop.code=0&rpchrome.code=0&rpgoogletb.code=0&clickpotato.code=0&SrS3x.code=0&SrS31.code=0&SrS2x.code=0
We can see in it, most likely:
- the browser: "IE.6.0"
- the OS (XP): "5.1"
- the MAC address (00-03-FF-4B-E1-AF): 00-03-FF-4B-E1-AF
- the country or keyboard layout: Fr!
- the filename that has been downloaded: ""VLCSetup.exe". This could probably mean the guys have various malicious files reporting to the same server...
- then comes what looks like a software inventory: realplayer.code=0: no realplayer found installed? / rpwcdesktop.code=0: I don't know :( / rpchrome.code=0: no Chrome installed? / rpgoogletb.code=0: no Google Toolbar found? / clickpotato.code=0: no "clickpotato" installed.
Well, it appears they create a profile of the computers...
Let's move on the installation procedure. If you run the file vlcsetup.exe (which I advise you no to do!), the following window will appear, it is obviously quite different from the official/real VideoLan installer!
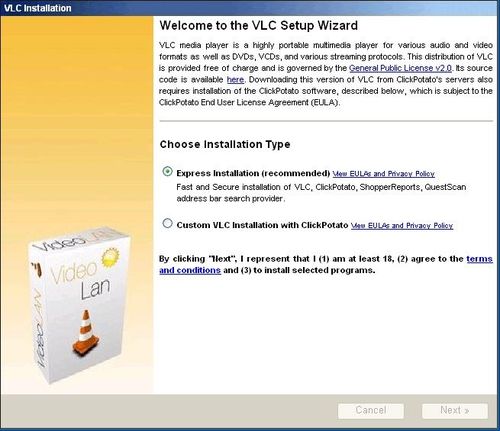
The button "next" triggers far more than a simple software installation:
- Domain ics.clickpotato.tv
HTTP GET /Software/SrS2xParam01/434/ShprRprt.exe?rnd=2296111
HTTP GET /Software/QuestScan/496/brand.exe?rnd=2323420
HTTP GET /Software/ClickPotatoLiteClient01/492/ClickPotatoLiteInstaller.exe?rnd=2340385
- domain upgrade.questscanone.com
HTTP GET /download/questscan/1_26/questscan-setup.exe 9446 1599.561490
HTTP GET /download/QuestScan/1_27/upgrade.cab?upg=path
and last! HTTP GET /Software/VLC/466/vlc-1.1.9-win32.exe?rnd=2368105